Scripting languages and viruses
Do you remember the Dropping Elephant malware?
Attacking China’s foreign relations, it used the AutoIt scripting language and exploits from 2012 and 2014 to steal relevant data and documents from the infected computers.
While being technically weak, it still managed to stay undetected for some time, thanks to the scripting language of AutoIt that is incredibly hard to analyze for all the anti-virus solutions.
It also managed to execute arbitrary code using old exploits that have been patched for a long time.
Let’s try that to create a counterfeit virus and see how anti-malware softwares would react. We’ll use some local privilege escalation with a March 2016 exploit : MS16-032.
Interesting enough, the powershell version of that exploit isn’t even detected by many AVs, 4 months later.
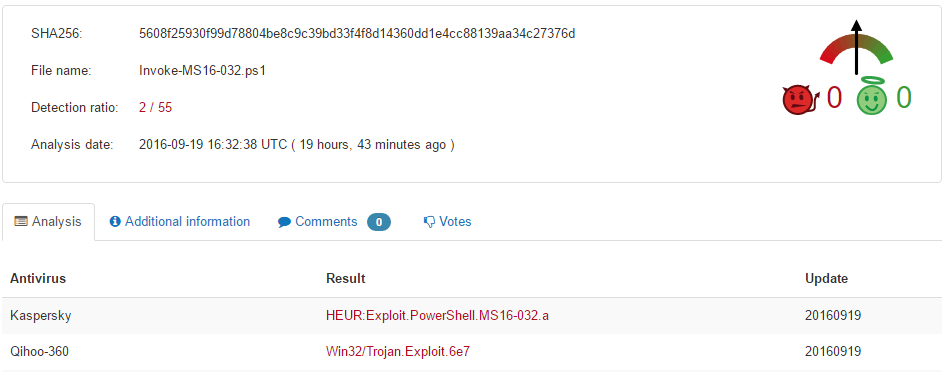
And here comes PS2EXE, a small Powershell utility that “encapsulates a script with a lightweight PowerShell host written in C# and compiles the dynamically generated C# source code in memory to an EXE file”.
Let’s change the behavior of our Powershell exploit so that it adds itself to startup as admin, and compile it. How are the results? Alarming.
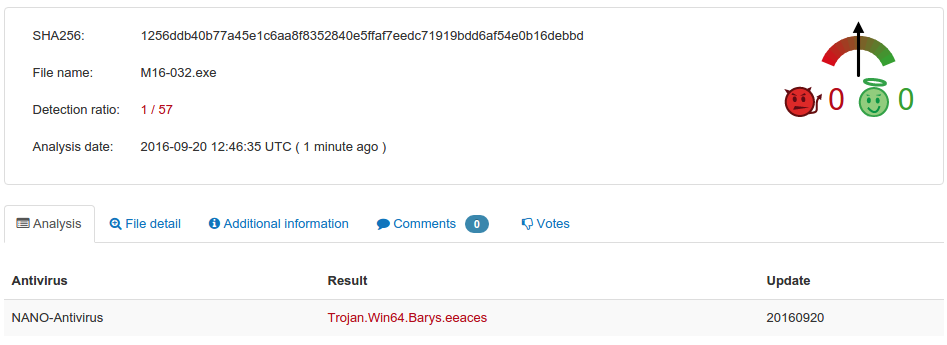
To make it even worse, let’s package our fake virus with some RAT utilities into it, using Node.js and nexe to compile the whole package.
The only downside to compiling a Node.js application is that the resulting executable is pretty big, which would make it easier to detect (16MB here).
However, with an appropriate packer and some compression it could definitely be sneakier.
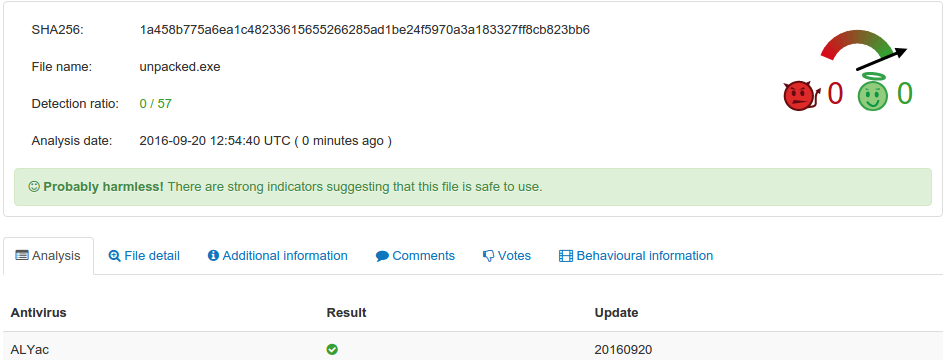
… I guess it means that we’re gonna see more and more script viruses in the future.